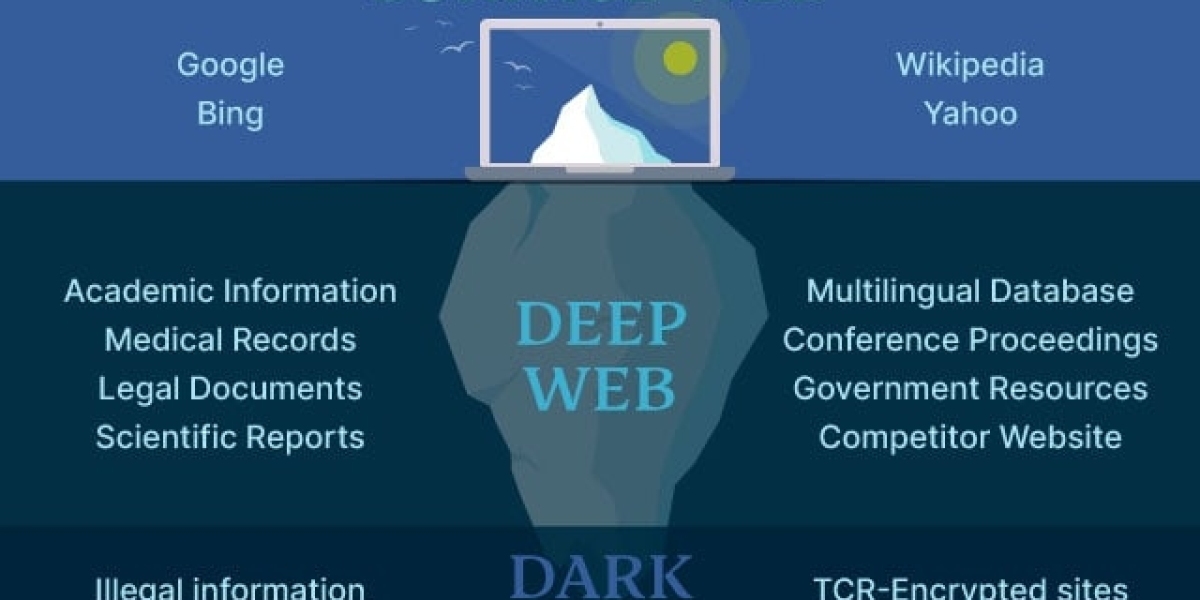
Navigating the enigmatic depths of the Tor network unveils a digital realm shrouded in anonymity and intrigue. Tor, short for The Onion Router, is a specialized network designed to enhance privacy and security by routing internet traffic through a series of volunteer-operated servers, rendering the user's online footprint virtually untraceable. Delving into the Tor network reveals a diverse landscape, where users can find a myriad of content ranging from legitimate and privacy-focused services to the more shadowy corners of the digital world.
One of the primary attractions within the Tor https://deepweb.net/blog/newest/what-can-you-find-if-will-search-in-tor-network network is the ability to access the dark web. The dark web encompasses a collection of websites that are intentionally hidden from conventional search engines. Here, users can find platforms offering a cloak of anonymity for whistleblowers, journalists, and activists, enabling them to communicate without fear of reprisal. The Tor network plays a crucial role in safeguarding the identities of these individuals by providing a secure conduit for their online activities.
Beyond the noble pursuits, the Tor network is also known for hosting marketplaces that facilitate the exchange of goods and services, often in cryptocurrencies to ensure a heightened level of discretion. While some transactions are legitimate, the anonymity provided by Tor also attracts illicit activities, including the sale of illegal drugs, hacking tools, and counterfeit documents. Law enforcement agencies worldwide monitor these platforms to curb illegal activities, emphasizing the cat-and-mouse game that unfolds within the encrypted confines of the Tor network.
Exploring further, users may come across forums and communities that discuss sensitive topics without the fear of censorship. Tor serves as a sanctuary for free speech, allowing individuals in oppressive regimes to voice their opinions without risking repercussions. However, this freedom also opens the door to extremist ideologies, with various groups utilizing the Tor network to communicate and propagate their views away from mainstream scrutiny.
It's essential to note that not all content within the Tor network is nefarious. The network hosts legitimate websites, forums, and resources that prioritize user privacy and security. Services such as SecureDrop, an open-source whistleblower submission system, leverage Tor to ensure the safety of those disclosing sensitive information to journalists and media outlets.
In conclusion, the Tor network, with its multi-layered encryption akin to the layers of an onion, provides a unique digital landscape. Users can uncover a spectrum of content and activities within its depths, ranging from privacy-centric services to the more controversial and clandestine elements. Navigating the Tor network requires caution, as anonymity can be a double-edged sword, offering protection for noble causes while also providing a haven for illicit pursuits. As users traverse this hidden realm, the Tor network remains an evolving space where the delicate balance between privacy, freedom, and security unfolds in a complex interplay of technology and human behavior.